A guest network isn’t just for the paranoid, it’s a great idea to prevent you main SSID passphrase leaking and keeping your important IT kit more secure. You know, that special one with all the, ahem, research material. 😛 How far you want to go with the guest network is up to you really:
- Just a different IP range so you can tell guest/LAN apart
- Guest network isolated from LAN, maybe with one or two services permitted
- Guest clients isolated from each other.
To do the above your going to need three things: a new network interface, new WiFi network and a new firewall zone. This can mostly be done via the web GUI but in order to do guest isolation (i.e. guest A can’t see guest B), you will need SSH access to quickly update one file. This is all well documented on the OpenWRT site, although the screenshots are out of date now.
Following along the main parts of the web GUI steps, we start with defining a new WiFi Network.
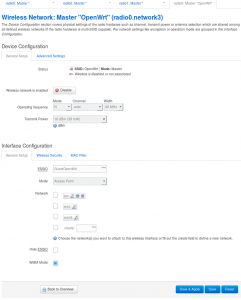
Creating a new wireless network is a simpl affai, although you can only select one mode of operation.
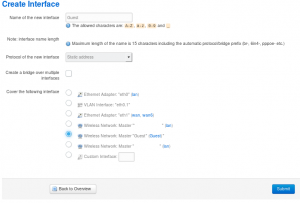
Next, we define a new interface and assign that to our Guest network.
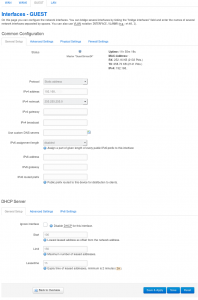
And then drop into the new interface to make details changes.
After this, it’s really just a matter of tweaking the the Firewall, which is well detailed in the web steps.
If you want to do isolation between Guest network clients, it’s a simple case of adding “option ‘isolation’ 1” to the relevant config section in “/etc/config/wireless” as details in the CLI guide. The OpenWRT documentation is really clean and well laid out, following along even with the older screenshots is pretty easy.

Leave a Reply
You must be logged in to post a comment.